Outsourcing Surveillance: A Cost-Effective Strategy to Maintain Maritime Supremacy

All militaries watch other militaries. They do so to learn how their allies and adversaries move, train, and operate. By understanding another military’s “pattern of life,” they learn about weaknesses and vulnerabilities that can be exploited later in conflict (or with allies, they learn about and incorporate sound military practices).
The Russo-Ukrainian war has confirmed what was already widely known about this age-old practice: Valuable surveillance is difficult to maintain over long periods of time. It demands both assets and money. Naval surveillance in the Russo-Ukrainian war is further complicated by the fact that a third party — Turkey — controls access to the territorial sea — the Black Sea — bordering the conflict zone and that Ankara has chosen to remain neutral in the conflict. No matter how difficult to maintain, however, surveillance of the Black Sea and its environs remains critical for Ukraine and its allies. Taking as a given that Turkey will deny traditional U.S. Navy vessels access to the Black Sea for the conflict’s duration, we believe a bit of creativity is warranted to maintain persistent surveillance in the region.
The U.S. Navy could pursue two interrelated policies to achieve this. First, it could outsource a significant amount of surveillance tasks to both American and allied merchant vessels. Second, the United States could deploy small numbers of marines or special operations forces on allied vessels and equip them with military and commercial-grade sensors for surveillance. These partially outsourced surveillance systems could also be scalable for other contingencies around the world to support broader U.S. interests and increase global surveillance.
The first approach is loosely modeled on the Chinese government’s use of a maritime militia for surveillance and based on a simple idea: The U.S. military could leverage more sensors deployed all around the world in lieu of building expensive platforms to house them. The second is a variation on the “light footprint” model that special operations forces have used to great effect around the world to support U.S. Air Force air campaigns. The two approaches could be used far outside the Ukrainian context and would reinforce extant experimental efforts by the Marine Corps to demonstrate an agile and stand-in force aboard non-U.S. vessels in the Barents Sea. They could also be a useful tool to capture more surveillance data at a more manageable cost around the world — these approaches would expand U.S. Navy sensor capabilities without building more ships or other platforms. The Navy could “flood the zone” with cheap systems that, in aggregate, could yield great dividends for NATO and U.S. allies around the world — not only vis-a-vis the current Russian war against Ukraine, but also in the Indo-Pacific.
Capitalizing on basic sensors and link architectures, the costs associated with a partially outsourced surveillance system are much less than the hundreds of millions of dollars spent on deployment operating costs. This approach would have to overcome obvious problems, such as the need for encryption (where applicable) and ensuring that each participating platform can communicate with military assets. There is also the potential for attacks on commercial shipping, particularly those that would host U.S. military sensors. While the main benefits of merchant shipping surveillance would be enjoyed up to the point of conflict, we believe that the risk of military skirmishes after that point can be managed with a two-tiered system. When the United States is not a party to the conflict, the threat to commercial shipping is low. This has been the case during the Russo-Ukrainian war. If the United States were party to a conflict, the mission could transition to smaller deployed teams on allied vessels working in concert with the United States, willing to host U.S. forces.
Persistent Surveillance
Speaking broadly, persistent surveillance is one of the most valuable types of surveillance missions. If (and when) it is time to strike, the surveilling military gets to plan the first move on its own terms while enjoying the element of surprise and initiative. Generally, the value of data is correlated to the size of the territory covered and its continuity. The larger the coverage gaps, the less valuable the data that is being collected.
Persistent surveillance is a challenging problem for two reasons: capacity and cost. It takes a good deal of assets to look at large areas (for instance, the 169,000 square miles of the Black Sea’s surface). For the U.S. military, its global presence and preeminence require a broad spread of assets, compounding the capacity issue for a given region. There simply are not enough U.S. resources to stare at any one area indefinitely, as has been evident in prior conflicts.
The second reason is cost. Striving for omnipresence is expensive. When looking at manned intelligence and surveillance air platforms, this is particularly acute because the recurring costs per flight hour are so high (because of fuel, manpower, maintenance, spare parts, and beyond). One 2020 study found that the recurring cost per flight hour of manned platforms ranged from $30,000 to over $100,000. Meanwhile, availability of military aircraft has decreased over the last decade. This is not to suggest that deploying manned (and unmanned) aircraft is not worthwhile. It is. However, it is a hard reality that deployments bring substantial operating costs, and intelligence and surveillance missions represent only a fraction of what those U.S. military assets perform. A perfect example of this is the P-8A, a surveillance asset whose primary mission is actually anti-submarine warfare.
As both the war in Ukraine and the rising tensions in the East and South China Seas show, the need for surveillance to both understand operational deployments and monitor belligerent actions is only increasing. The United States, put simply, cannot be everywhere all at once. Yet, it has global interests that require persistent monitoring.
Given today’s political climate regarding the national debt and defense budget, simply increasing U.S. military capacity is not tenable. By increasing the number of sensors globally, the Department of Defense would not only gain valuable, near-persistent surveillance data in areas of interest at (relatively) affordable prices, but also would enjoy the option of gray-zone operations given the strategic ambiguity that outsourcing provides.
Variations on a Theme: Maritime Militias
The Chinese government has used a maritime militia to expand its reach into the South China Sea. China’s use of these militias is destabilizing. However, there are some advantages to having ships “deployed” in a lot of places. The ability to leverage commercial ships is of particular interest to us — and for many who think about how to deploy naval power around the world.
Comprised primarily of fishing vessels, the Chinese maritime militia frustrates freedom of navigation and trade between the United States and its allies. Its use is also a brilliant “defense-in-depth” strategy that enables deniable misbehavior in peacetime while providing the Chinese government with cheap and omnipresent reconnaissance and surveillance in preparation for conflict.
There has been much discussion on how to negotiate the challenge posed by China’s maritime militia, from employing the U.S. Coast Guard to training unconventional partner forces as sanctioned by the National Defense Authorization Act. What we find more interesting is trying to glean teachable lessons inspired by the maritime militia’s existence, and apply them to the U.S. military:
1) These ships are cheap and provide surveillance data to China’s military, which means the People’s Liberation Army Navy has effectively deputized non-military vessels — economically.
In comparison, when the U.S. Navy looks at building out its footprint, it is often looking at new ship construction. The new FFG(X) frigate will cost around $800–900 million. Even used military cargo ships cost around $60 million each. This comparison is, admittedly, not perfect. However, it is important to think through how to address key challenges the United States faces with longer-term shipbuilding, along with the need to sustain a viable footprint around the world to counter its adversaries.
We believe that one way to approach this problem is to increase U.S. capabilities through increased delegated presence rather than new construction. As China’s maritime militia demonstrates with its large number of deputized fishing vessels (the primary class of militia vessel), increased capacity is itself a remarkable capability — particularly when the sought-after capability is putting watchers on the water. Where on a given day there are perhaps 10 Chinese combatants patrolling a given water space, ostensibly there are now scores more once the maritime military is taken into account — at a relatively cheaper cost to Beijing (which does not adequately fund the militia to begin with).
Similarly, if the United States outfitted merchant ships that are already conducting trade through sea lanes around the Mediterranean and Black Sea with a rack of equipment and perhaps an extra radar, the cost of increased surveillance would be one to two orders of magnitude less per ship than if done through new construction. The same is also true for deploying small numbers of marines or special operations forces on allied ships, thereby enabling more U.S. presence in more places without having to send U.S. Navy ships to every global hotspot. In addition, commercial shipping and merchant vessels have greater endurance (and are more robust) than fishing vessels. The adaptation is a leg up from the Chinese maritime militia, as the merchant vessels can go much greater distances and enjoy longer sustained speeds.
2) The use of non-military vessels also gives the sponsoring country a patina of deniability. In the Chinese case, the government uses its maritime militia to provoke third countries, but can plausibly claim that aggressive actions are taking place outside direct control.
The maritime militia have direct ties to the Chinese government, but can also pose as free agents, acting on their own. Accordingly, the Chinese government has the ability to shrug off responsibility for any actions the international community views as harassing or otherwise escalatory. This provides a derived benefit to the government to exercise diplomatic offramps from escalation.
In a similar way, this model of surveillance would be especially valuable where an overt U.S. military presence may be denied or deemed escalatory, as is now the case with the Navy in the Black Sea. For example, a commercial merchant vessel could identify a military plane flying overhead via numerous methods, both passive and active, without sparking conflict. Using radar is an active method — and therefore detectable. Using electronic warfare support measures or visual identification are passive methods — when these are used, the surveilled plane or ship is none the wiser.
Even with active methods such as radar, depending on the frequency of emission, it becomes difficult to discern the emission’s exact origin in a place with as much electromagnetic noise as the Mediterranean Sea. Based on one of the authors’ experience, it is like searching for a needle in a stack of needles. The U.S. Navy could deny any involvement while still gleaning valuable surveillance data.
3) The use of many individual sensors in different locations spins an integrated surveillance web that covers a greater span of area than that exploited only by military vessels.
For the Chinese government, the amount of ocean needed to monitor maritime claims is substantial. Bringing militia forces into the fold bolsters the number of patrollers at a given time — the Chinese Communist Party does not need to rely on naval or coast guard units alone. It is a solution to a simple numbers and search rate game. Increase the number of pieces, increase the search rate. For the reasons previously discussed, the U.S. Navy could also benefit from applying the same principle in areas it cares about.
On the other side of the world, the Russo-Ukrainian war has reinforced the need for mass and redundant surveillance platforms to withstand attrition and to respond quickly to the needs of commanders. Considered in concert with the numbers and search rate issue for a water space of interest, the adaptation of outsourced surveillance is particularly useful. The importance of this is best shown graphically.
Take these figures that show open source shipping data via the Automatic Identification System in the vicinity of the Black Sea. The first graphic shows all shipping vessels that are reporting their position using this system. While some tracks are older, the density of vessels makes clear the potential for coverage by merchant vessels in this NATO area of interest. The second figure shows the overall shipping density of the Black Sea.
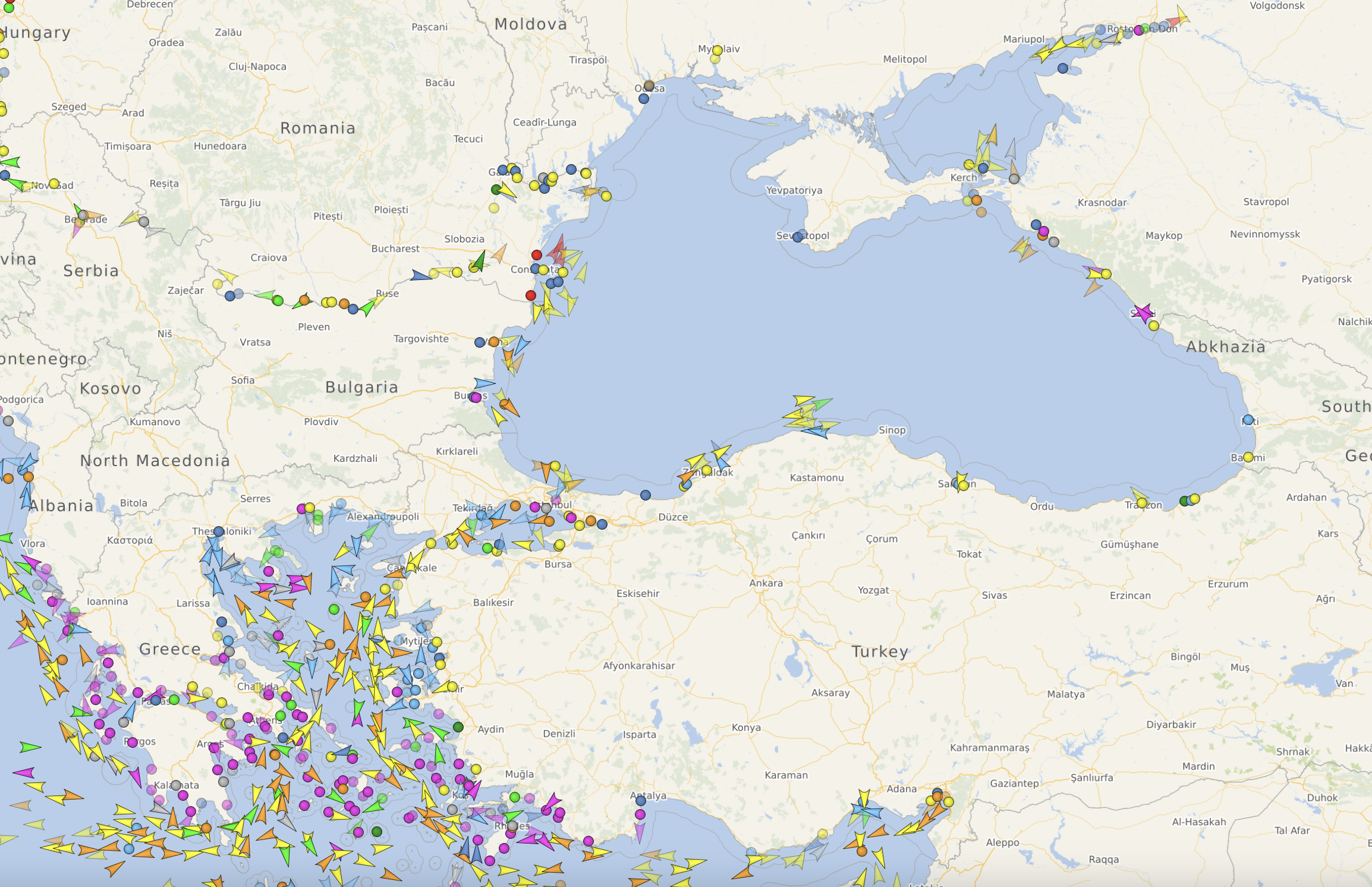
Figure 1. All Reporting Shipping Traffic IVO the Black Sea and Med Sea (4 Oct 2023, 0050Z)
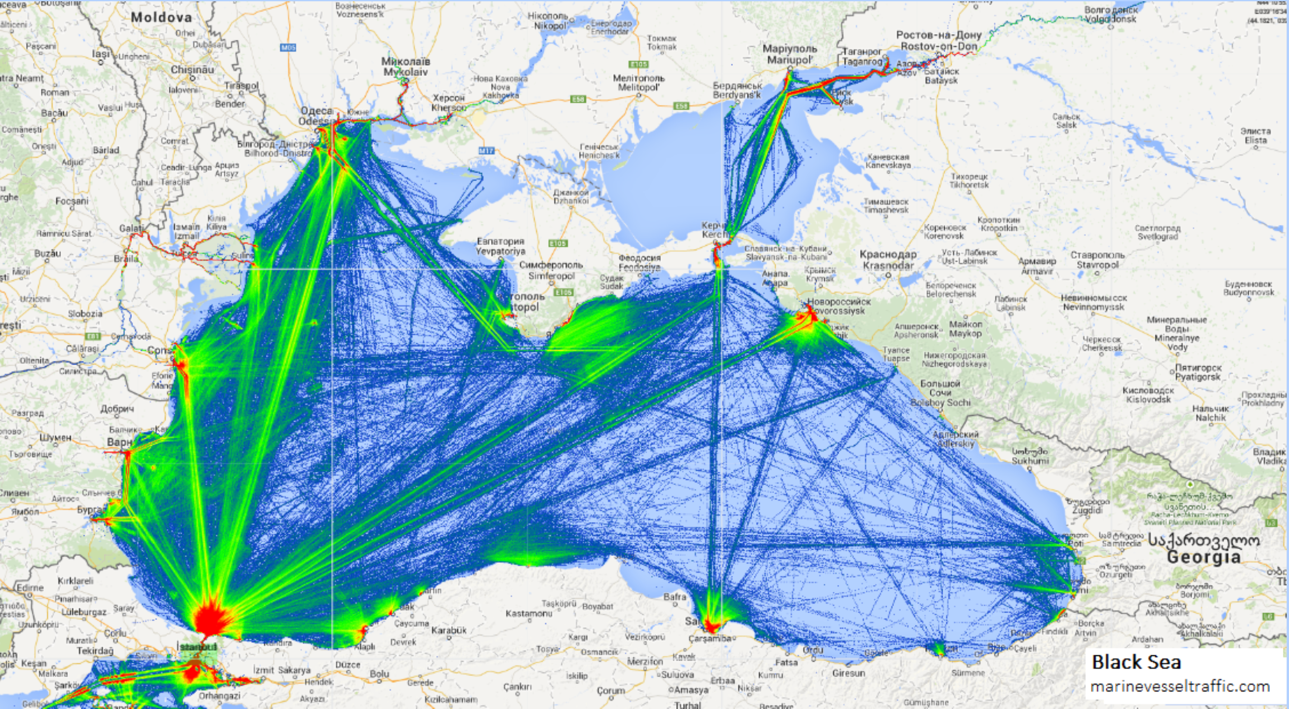
Figure 2. Overall Shipping Density of the Black Sea
As figure 2 suggests, equipping these vessels with surveillance equipment could knit a perfect surveillance web using deputized commercial shipping.
4) Surveillance is the first step in the kill-chain. Put simply: You have to have a target to shoot at, which means targets have to be found before a weapon can be programmed to strike it. Speaking from a Western perspective, this is where China derives the most value from its maritime militia.
The common kill chain discussed in American military thought is “find, fix, track, target, engage, assess.” In particular, the first link in the chain is germane to U.S. and allied merchant vessels. If conflict breaks out, the near-persistent surveillance web afforded by merchant shipping would allow the surveilling military and its allies to locate enemy combatants and communicate what those enemy combatants are doing. In instances where multiple merchant shipping vessels have located an enemy combatant at the same time, this produces a collaborative location that is relatively more precise. At that point of “find,” the combatants could be handed off to allied military assets to further fix and convert to a track, and then dispatch at their discretion. This is the heart of the advantage that persistence surveillance affords. But equally importantly, if done in this manner, it is done relatively on the cheap.
Pre-conflict (most of the time the U.S. Navy would use outsourced surveillance), the surveilling power would enjoy cost savings associated with not solely using military assets. The commercial surveillance web would have the most utility up until conflict erupts, because it would give the U.S. Navy insight into the initial lay down of enemy combatants prior to attack and help better inform enemy behavior. Reconnaissance and surveillance become a very different game once conflict is underway, and rightly should be done in the non-civilian realm.
Civilian risk can be minimized in various ways. Once conflict breaks out, notice to mariners bulletins should broadcast across marine traffic nets, informing merchant shipping that risk of crossfire exists (and to stay clear). Any merchant shipping that continued to surveil would presumably be those with marines or special forces contingents aboard. Regardless, in the case of the Black Sea, even if the Russian navy suspected some merchant vessels were participating in U.S. surveillance activities, it would be a large gamble to preemptively attack merchant ships. Looking for needles in a stack of needles is hard enough, but to decide to attack any and all needles is a gamble that even Russia would be hesitant to make. The apparent wanton destruction of NATO merchant vessels would be a quick way to pull NATO into a larger conflict.
A Cheap(ish) Riff: Deputizing NATO Merchant Traffic to Outsource Surveillance
A partially outsourced surveillance web would consist of many nodes. In the case of the Black Sea and East Mediterranean, these nodes would consist of U.S. and NATO merchant vessels and military vessels, as well as military aircraft. Each node would have a sensor package, which would vary depending on the class of the surveilling vessel (commercial or military). If the objective was to detect combatant vessels and aircraft, then the basic sensor package would include visual observation tools (like binoculars), the automatic identification system, and possibly a basic air surveillance radar. Virtually all surface vessels have surface radars that can detect seafaring traffic for navigational purposes. All three of these methods use commercial off-the-shelf material and do not require any kind of cryptologic material to operate.
Using its sensor package, a node could detect any contacts that come into its field of regard. The next sequence in the surveillance web would be for the node to aggregate the contact data. This could be done on a laptop with a basic computer program that correlates and displays contacts in space and in real time, using an operator interface. Contacts could be detected via the automatic identification system and radar and automatically fed into the software, or entered manually based on visual sighting. This collection of contacts would form the node’s operating picture.
The next step would be the dissemination of data. This could be done in multiple ways. The simplest would be using voice reporting on a radio. This could be on a frequency akin to an “all call” or “Fleet Tac” net, or to designated military nets used by maritime patrol forces. Another would be via the automatic identification system. A third — and this is our preference — would be via a third-party application, based on commercial software, that would pass the position, course, and speed of any reported vessel via encrypted messaging, such as on Signal or Telegram. This approach could also circumnavigate classified cryptologic challenges and would just require an additional laptop kit aboard the military units and use open source methods to pass data.
The most effective military-grade option would be employing a tactical data link. This option should be reserved for the marines or special operations forces deployed on allied vessels in what we’ve dubbed the “light-footprint approach.” NATO uses Link-22, which is the follow on from Link-11. By using a radio and a data link terminal, contacts could be transmitted over the ultra-high frequency or high frequency spectrum. These messages could be received, collected, aggregated, and further disseminated to fuse what is known as a common operating picture.
This kind of system is how near-persistent surveillance is realized. Reporting units in the data link are now no longer simply a score or two of military units. Patterns of life for military assets coming in and out of the Black Sea and Syria would now be much more frequently, easily, and cheaply stitched together. For any of these imagined methods, it is also worth mentioning that the National Security Administration also offers commercial solutions for classified programs, which makes the security aspect of such data exchange that much more viable a possibility.
We envision that the equipment necessary would be procured and installed by the surveilling NATO country, but the training and select usage could be done by various special operations units or marines within the NATO alliance. The U.S. Navy is particularly adept at the “train the trainer” model of fleet integration. Furthermore, in September of this year, Secretary of the Navy Carlos Del Toro announced the standing up of the Disruptive Capabilities Office, which will “push the bounds of rapidly delivering warfighting capability though the innovative application of existing and new systems” and “through rapid experimentation and prototyping … will work collaboratively with stakeholders from across our department focusing on delivering solutions to our warfighters at a pace and scale to close our fleet’s most critical capability gaps.” Such an office could also be an invaluable facilitating entity here.
“Yeah … But … Would This Even Be Legal?”
The Geneva conventions stipulate that non-combatants such as medics or chaplains cannot carry firearms (and implicitly therefore, cannot actively participate in armed conflict). Another issue may stem from the fact that those caught committing acts of espionage are not granted prisoner of war status. And, so, the line of thinking goes: if the U.S. military and its allies frown at China’s use of a maritime militia as it blurs the line between combatant and non-combatant, how would it be acceptable for U.S. and NATO forces to adopt a similar playbook?
This is answered in two parts.
First, the way China employs its maritime militia and how NATO would employ its partially outsourced surveillance web are fundamentally different. The former uses its militia not only to surveil but to harass other countries. NATO would use its web for surveillance only. There is no prohibition on using commercial vessels to provide intelligence, including surveillance data. Further, even if hostilities escalated from peace time into armed conflict while the outsourced surveillance web was in use, there should be no legal issue. Surveilling merchant ships detect radar “blips” or visual sightings of combatants. They report these to a given net as contacts. U.S. or allied military assets would then take over updating and subsequent reporting of those contacts, refine and convert the contacts to targetable tracks, and, while maintaining reporting custody of those tracks, employ fires as directed. There is an important degree of separation between this and the Chinese approach.
Second, there is an attitudinal attribute to the question above. If NATO were to take a page out of China’s playbook and embrace gray-zone behavior, would that give the international community the impression that NATO is no better than China when it comes to military deportment? Does NATO, then, lose credibility?
To this, the answer should still be no. NATO’s use of the outsourced surveillance web would have a very specific scope of service in mind: aggregating surveillance data. With the challenges posed by both Russia and China, maintaining maritime superiority is only becoming more challenging — and more critical — as resources are fast becoming limited and more expensive. In the end, outsourcing surveillance is a simple business decision.
Conclusion
The United States has a need for military surveillance, but the most valuable forms of surveillance are costly and require significant resources. To address this, the U.S. military and its allies could scale up from the fundamental thesis of China’s maritime militia and outsource maritime surveillance in select locations vis-à-vis merchant shipping. Such a bold maneuver would enable a great increase in surveillance (in desired locations) at a fraction of what it costs to increase military vessel procurement. Using these vessels for surveillance only, all the way up to the beginning of a conflict, would spare the West from the same international finger wagging that China often receives.
We envision that this outsourcing would be used primarily in the recurring preparation of the operational environment, prior to hostilities taking place. This is where the United States and its allies find themselves today. Should conflict become imminent, this surveillance web would afford the U.S. Navy and its allies a better-informed first strike advantage, without the total tail cost associated with massing military units for the sake of surveillance. And should continued surveillance webs be necessary, a much smaller subset of vessels with marines and special forces aboard could negotiate that risk.
The military is a business and sound business decisions are important, as is thinking creatively. Audacity has won many a contract and made many a company wildly successful. It also can enable the United States to win big in the realm of surveillance, if played correctly.
Cdr. Josh “Minkus” Portzer is a P-8A weapons and tactics instructor in the U.S. Navy. The views expressed here are his own.
Aaron Stein is the chief content officer at War on the Rocks.


