

“I think what you’re going to see is that Russia will be held accountable if it invades. And it depends on what it does. It’s one thing if it’s a minor incursion and then we end up having a fight about what to do and not do, et cetera.” Those words from President Joe Biden set off a firestorm from Washington to Kyiv, as critics — including Ukrainian President Volodymyr Zelensky — worried about the repercussions of the United States and NATO distinguishing between an invasion and a minor incursion when deciding how to respond to Russian aggression. Clean-up efforts tried to “clarify” the comments by hurriedly resetting messaging back to vague threats of serious repercussions. However, the president’s words had already revealed the unmistakable challenge that is managing interstate conflict with actors who are increasingly capable of operating near, or beneath, the threshold of traditional armed war.
The way that states advance their interests in this so-called “gray zone” has continued to grow in importance to warfighters and policymakers. Recent events along the Ukrainian-Russian border are only the latest in a long list of international incidents and ongoing campaigns that could be characterized as gray zone activity. Correspondingly, there is a rapidly expanding body of work describing what the gray zone is, why states choose to operate in it, and how to defend against such actions. Namely, aggressors in the gray zone mix political, economic, information, and military tools to advance their interests while presenting opposing policymakers with unsavory escalation dilemmas.
Less studied, however, are the specific challenges that gray zone campaigns pose to intelligence officers. Certainly, the “gray zone” is nothing new for intelligence — it does, after all, encompass cornerstones of the intelligence business: disinformation, denial and deception, and covert action. Nevertheless, managing the contemporary gray zone means contending with how the development and proliferation of emerging and disruptive technologies is rapidly transforming it. As we recently wrote, technology is accelerating the speed, sophistication, and spread of gray zone activities globally, uniquely challenging the fundamental functions of intelligence agencies to detect and understand threats. This includes the ability to identify and attribute indicators of hostile activities as they emerge (detect) and to contextualize them within a broader understanding of an actor’s strategy and intentions (understand).
Ideally, these functions should be simultaneous and mutually reinforcing. That is, information collected will inform strategic insights in real time, and those insights will enable better-informed analysis and collection. However, if you imagine this detect-understand relationship as a wheel, the volume, speed, and complexity of modern gray zone activities act as friction. The wheel slows as threat indicators become increasingly subtle and ambiguous. In terms of real world consequences, this may mean missing a short decision window to intervene during the early stages of an economic, information, or cyber campaign. If intelligence agencies are to accelerate the wheel to keep pace with gray zone threats, a series of technical, organizational, and cultural intelligence reforms are in order.
In support of efforts to address these pressing challenges, we recently undertook an eight-month research project studying intelligence in the gray zone. After interviewing dozens of experts — including several current and former intelligence officials — and conducting a structured workshop in late 2021, we formulated several recommendations for the U.S. intelligence community to develop the tools, organizational structure, and culture capable of both detecting and understanding gray zone activities. While our research primarily focused on how the United States should modernize its intelligence mission for this era, we nevertheless believe these findings and recommendations have broad applicability for other nations facing similar gray zone challenges.
Creating a Gray Zone Lingua Franca
Admittedly, the “gray zone” is an imperfect term. Its most basic definition as everything between peace and war means it encompasses an exceptionally broad spectrum of activities, ranging from the indistinguishable to the outright brazen. At the same time, identifying when an activity should be characterized as in or out of the gray zone is not necessarily straightforward. After how many Facebook posts (or election cycles) is Russian misinformation so commonplace so as to be downgraded from a gray zone activity to one of routine statecraft? As the nature of both statecraft and warfare evolves, the gray zone goalposts are constantly moving.
That is not to say that definitions are not important. On the contrary, a clear and consistent vocabulary to describe activities conducted within (or on the fringes of) the gray zone is necessary to efforts to identify, aggregate, and measure such activity using standardized methodologies. The alternative is a gray zone Tower of Babel, where varying terminology between intelligence agencies, the private sector, allies, and academia undermines efforts to unify analysis; allocate scarce resources; and develop effective, risk-informed policy.
To establish a gray zone lingua franca, we recommend that the Office of the Director of National Intelligence leverage existing processes, including the National Intelligence Priorities Framework, to develop consistent terminology for categorizing and defining categories and types of gray zone behavior. Through the National Intelligence Priorities Framework, this typology can be integrated across global intelligence collection and analytic priorities and requirements.
We are clear-eyed about the level of effort such an undertaking would require. Interagency, multidisciplinary attempts to codify standardized threat definitions can be, to put it mildly, challenging. Moreover, unifying the language we use to describe activities that are often designed to evade clear categorization (and that may materialize very differently depending on the actor, domain, and location) will not be easy. Thankfully, the proposed unification is not without precedent. For example, the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) framework has emerged as a standard lexicon for capturing the exceptionally diverse and continuously evolving range of computer network intrusion techniques. In an arena defined by blurred lines, clear guidance on how to describe gray zone threats and the levels of risk they pose will be crucial to collecting, analyzing, and communicating intelligence information.
Detecting Gray Zone Threats
Today, intelligence officers are overwhelmed by data. Global data generation increased more than 30 times over the past decade and, by 2025, it is projected to double again to 181 zettabytes. To put this number in perspective, a common external hard drive is approximately a 1/2 inch tall and stores one terabyte of data, equivalent to about 75 million pages of text. The number of these hard drives needed to store the world’s data in 2025 would pile from the Earth to the moon and back three times.
Unable to contend with the data challenge, intelligence analysts may struggle to identify what information is relevant or may fail to deliver fully informed judgments. Gray zone threats are particularly tricky because they often manifest as otherwise routine diplomatic, economic, or commercial behavior. And even if an intelligence officer knows what to look for, they may not know where to look. In the 21st century, much attention has rightfully shifted to the data commercial remote sensors, social media, public records, and cyber forensics produce as potentially valuable sources of intelligence information. In the future, this diversity of data will continue to grow, led by the further development of smart cities, the Internet of Things, and smartphones.
Institutionalizing means to widely distribute knowledge of new, unique, and valuable data is necessary to contend with gray zone threats that may manifest across any number of domains. To this end, we recommend that the Office of the Director of National Intelligence sponsor an intelligence community-wide collaborative open-source intelligence data catalog. Unlike other intelligence disciplines or specific lines of collection, no single intelligence agency owns open-source. For this reason, it is a discipline uniquely suited to catalyze increased collaboration and analytic integration across the 18 members of the U.S. intelligence community. The proposed catalog would serve as a centralized warehouse of datasets, facilitating rapid discovery of information organized at the functional, country, regional, and global levels.
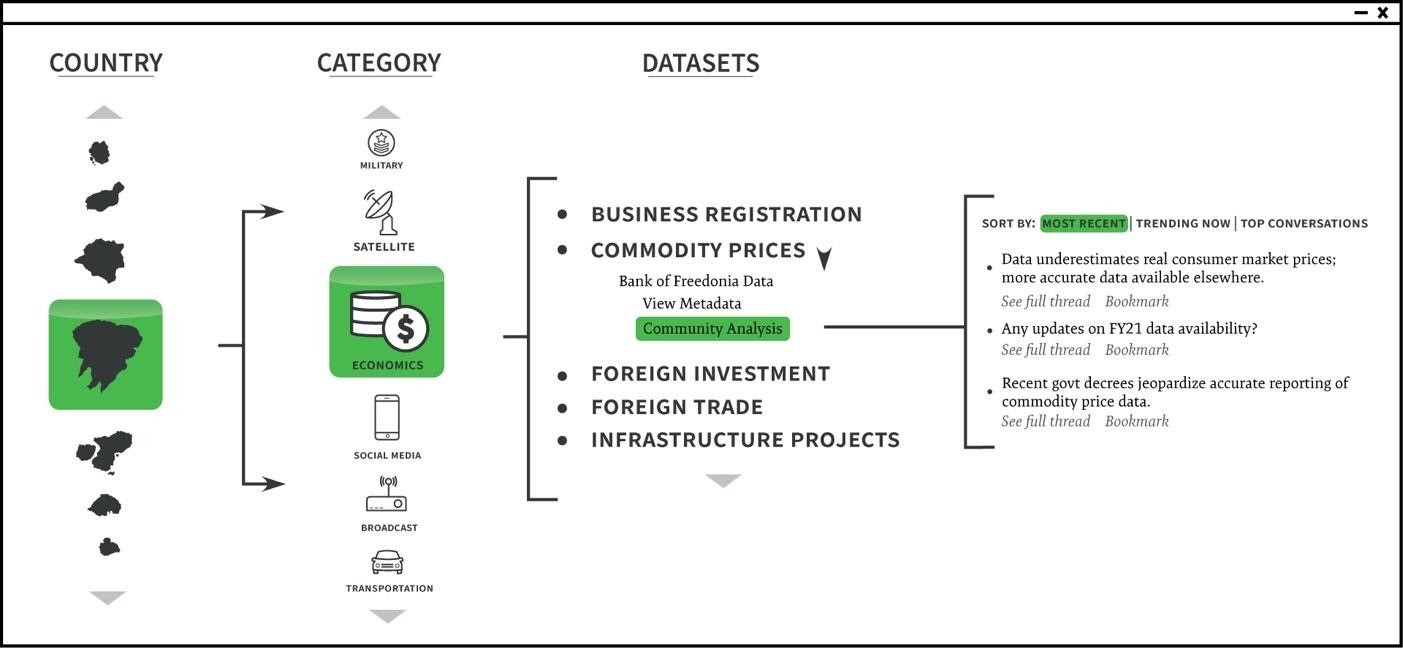
Representation of a hypothetical open-source intelligence data catalogue, with datasets organized into categories and accompanying community-generated analytic perspectives. (Source: CSIS International Security Program)
Historically, assessing the objectivity and reliability of foreign broadcast media outlets has been a key element of open-source analysis. Building on this legacy, the proposed catalog would be overlaid with collaborative tools, allowing analysts to contribute their perspectives on data quality, reliability, and timeliness. As an example, the availability and reliability of public records may vary substantially from one country to another. Therefore, when looking for certain categories of data (e.g., business registrations) across multiple countries, such information could vary depending on what data is available, where it is generated, how it is captured, and who has access to it. A dataset that is recognized for its reliability and integrity would be credited as such in the catalog. Another that is known to be inaccurate, perhaps due to concerns about the reliability of the source, would be flagged accordingly. These judgments will help intelligence officers properly assess the reliability of different open-source datasets and will draw upon insights from forward-deployed, in-country personnel familiar with the host government, politics, and culture, as well as headquarters analysts responsible for conducting global-level analysis.
Expanding the Intelligence Universe
The quality of intelligence collection, analysis, and warning emerging from non-government entities is rapidly improving. Emerging technologies are delivering increasingly granular remote sensor data, cyber threat information, social media data, and an endless stream of digital exhaust. A wide range of entities have put this data to use in conducting in-depth, sophisticated analysis. Examples include Bellingcat’s efforts to expose Russian intelligence operations, HawkEye 360’s analysis of potential illicit fishing near the Galapagos Islands, and Mandiant’s analysis of the 2020 SolarWinds hack. Intelligence agencies and officers cannot — and should not try to — compete with this open-source revolution.
Instead, the U.S. intelligence community should seize the advantages of an expanding intelligence universe by reinvigorating efforts to incorporate a broader range of perspectives into forecasting and warning. The U.S. government has evaluated various geopolitical prediction and forecasting platforms for more than 20 years. However, the concept is most mature within the United Kingdom through its platform Cosmic Bazaar, which integrates forecasting predictions from a wide range of government and trusted non-government experts. The potential utility of these crowd-sourced platforms will only grow as the quality and detail of data available to non-government analysts grow. If there is consensus that open-source intelligence will be a disruptor going forward, then the people and organizations analyzing this data — academia, non-governmental organizations, and the private sector — need to be enlisted as partners. Efforts to broaden and diversify intelligence work are not exclusively about improving the accuracy of specific analysis or predictions. In many circumstances, the value of collaboration can simply be the opportunity to share innovative analytic approaches with others. Toward this end, there is tremendous utility in collaboration that opens pathways for intelligence analysts to think about old problems in new ways.
Organization and Culture: The Bedrock of Modernization
Overall, the U.S. intelligence community should bolster efforts to empower and incentivize innovation and digital transformation. This includes sustaining efforts to recruit and retain diverse, digitally literate intelligence officers who can inject new techniques and expertise into the intelligence community. However, as in any case of institutional modernization, technology alone is not enough.
Defending against threats in the gray zone also requires new approaches to the relationship between intelligence and policy. This includes closely evaluating what types of intelligence products can most effectively support complex policy deliberations and decision-making under deep uncertainty. One study of American analytic culture highlighted how so-called “current intelligence” production, such as for the President’s Daily Brief, has become “all consuming,” leaving little space for analysts to conduct long-term, complex warning analysis. The late Robert Jervis shared similar skepticism in his studies of intelligence failure, noting that articles in the President’s Daily Brief often left “no space for background and perspective, let alone analysis of alternative possibilities.”
We highlight these criticisms not to disparage intelligence support to policymakers. Indeed, the struggle to remain relevant is an age-old dilemma for intelligence agencies, and — as long as consumers value a product — intelligence analysts should continue to produce it. Nevertheless, as Cynthia Grabo wrote 50 years ago, “Warning does not emerge from a compilation of facts.” Capturing the nuance of gray zone threats in particular requires a shift in intelligence toward more complex analysis. It also requires new paradigms to facilitate more meaningful dialogue between intelligence and policy stakeholders. One useful avenue to improve these relationships would be the establishment of ad hoc working groups to facilitate greater interaction between mid-level intelligence officers and policymakers.
Intelligence — particularly warning intelligence — does not always serve a useful role in decision-making. Intelligence agencies, for their part, are often blamed for continually predicting crises, perceived by some as a cynical effort to evade accusations of intelligence failure. Joseph de Rivera suggested that part of the problem was that the necessary “filters” to make sense of intelligence in support of policy needed to be delegated to “persons nearer the source of intelligence.” The proposed working groups are intended to serve this function as an additional “filter” for the exchange of intelligence and policy information.
We envision these groups ultimately augmenting — not supplanting — existing National Security Council-led interagency policy deliberations. Despite established processes for discussing policy at progressively higher levels, many of the intelligence and policy officers who inform decisions up to the Principals Committee-level would benefit from the ongoing exchange of both intelligence and policy insights.
The proposed groups would be crucial in accelerating the wheel that is the detect-understand cycle. Neither intelligence officers nor their policy counterparts have all the answers, but constant interaction between these two elements can inject better, more comprehensive insights into the relationships between various gray zone activities. For example, it is no secret that Chinese foreign investment in Latin America has significantly increased over the past two decades. However, despite knowledge of activities across diplomatic, economic, and military channels implicating multiple countries in this trend, concern appears to have peaked only recently. In fact, it appears possibly too late, as U.S. Southern Command’s 2021 posture statement describes a situation with few available options to reverse the trend.
The proposed mid-level groups would be charged with working through the long-term, dynamic, and complex security challenges exemplified by this case. By working across agencies, portfolios, and responsibilities, the working groups could be well-poised to connect disparate activities across space, time, and domains — all in the pursuit of a coherent understanding of where an adversary’s strategy is headed.
Moreover, robust, diverse intelligence-policy collaboration will ideally help avoid the worst of outcomes, such as groupthink, cognitive bias, warning fatigue, politicization, or outright intelligence failure. The National Security Council cannot realistically be sustained as the primary vehicle for ensuring ongoing, transparent dialogue across all stakeholders. If issues, like Chinese influence in Latin America, play out gradually according to the logic of a “salami slicing” strategy, then building additional venues to track complex threats over time — and setting shared thresholds for when higher-level warning or policy decisions need to be delivered — can augment existing processes and facilitate more effective policy and intelligence relations.
As tensions mount along the Ukrainian-Russian border, little can be said that is positive about the situation. If there is any upside, it is perhaps that the crisis is demonstrating what intelligence in the gray zone could look like. Over the past several weeks, the White House has repeatedly called out Russian disinformation and amplified the British assessment that the Kremlin intends to carry out a false flag operation to create the pretext for an invasion of Ukraine. Similarly, the State Department published two fact sheets debunking false Russian narratives about the crisis and the Department of Homeland Security issued warnings of possible Russian cyber attacks. Ultimately, the goal should be to expand these types of activities and, more importantly, to execute them earlier in the escalation cycle.
Although no amount of modernization can completely lift the ambiguity that blankets the gray zone, improving and diversifying the technology, expertise, and collaborative tools available to intelligence officers will enhance their ability to manage the complexity and uncertainty of the modern gray zone.
Jake Harrington is an intelligence fellow with the International Security Program at the Center for Strategic and International Studies (CSIS) in Washington, D.C. Riley McCabe is a research assistant with the CSIS International Security Program. This article is adapted from their recent research assessing the future of intelligence in the gray zone, published in “Detect and Understand: Modernizing Intelligence for the Gray Zone.”
Photo by Jonathan van Smit
