It’s About Time: The Pressing Need to Evolve The Kill Chain

“Holding on to the things that made us great in the past is not the way to make us great in the future. In fact, I can only think of one reason to stand still, and that’s if you want somebody to catch you.” –Gen. Mark Welsh, former Chief of Staff of the Air Force
At approximately 2 p.m. on April 7, 2003, two weeks into Operation Iraqi Freedom, Saddam Hussein was supposedly spotted in a Baghdad neighborhood. At 2:48 p.m. a B-1 bomber was re-routed to strike. By 3 p.m. there was a large crater at the target. This and tens of thousands of airstrikes in Iraq, Afghanistan, Syria, Libya, and elsewhere since have been made possible by a process commonly referred to as the kill-chain. In the military, this dynamic targeting process is generally referred to by the sum of its parts — find, fix, track, target, engage, and assess (F2T2EA).
In a culture that progresses through iterative employment concepts every few years (multi-domain battle being the latest), the kill-chain underpinning it all remains surprisingly untouched since its inception nearly two decades ago. Inescapably, all processes and concepts must be modernized or recapitalized to avoid obsolescence as underlying assumptions and variables inevitably change. For the kill-chain, that time is now.
Aiming for Crazy
Today’s F2T2EA kill-chain was born in the late 1990s when Chief of Staff of the Air Force Gen. John Jumper presciently recognized that more agile and responsive airpower would become a critical enabler to the joint force. Therefore, he set a goal of single-digit response times for using airpower to strike emerging targets on the battlefield. At the time, many viewed his objective as an unrealistic, if not insurmountable, feat. The gold-standard until then — known as “Time Critical Targeting” — held: “less than 60 minutes, gotta be good; 0-30 minutes, gotta be lucky and good; less than 10 minutes, gotta be crazy.”
With the benefit of innovation over the last two decades, this witticism is now amusing rather than impossible. “Time Sensitive Targeting” supplanted “Time Critical Targeting.” F2T2EA was adopted into Air Force and joint doctrine and the kill-chain rapidly winnowed into single-digit responses. In fact, the opening anecdote was lauded as medal-worthy just days after the event. Today, this happens as a matter of routine. So why the need to change?
The growth in sensor technology on virtually every air platform — whether an intelligence-gathering platform or not — has permitted non-traditional aggregation and assimilation of data that was inconceivable in the 1990s. These increased platform capabilities have truncated the individual dynamic targeting steps and blurred the lines to a point that questions the notion of the current looped-linear F2T2EA methodology. Today, many platforms can seamlessly perform most of these processes. Some can perform all of them: Think of an armed drone coupled with the venerable distributed ground station and the appropriate target engagement authority. This happens daily in Iraq and Syria.
Other times, platforms concurrently perform non-linear kill-chain functions. This underpins the Air Force’s Iron Triad — the Cold War era E-3 AWACS, E- 8 JSTARS, and RC-135 Rivet Joint constellation — where no one entity has all of the information. Think of an RC-135 aircraft detecting an electronic emissions signal from a surface threat. Its crew works to find and track the signal, while orchestrating a cross-cued sensor source to confirm and refine fidelity of the signal of interest. This could be through the E-8’s synthetic aperture radar or even by tasking a drone’s electro-optical sensors. Ultimately the end-state is to fix and target so that data can be turned into actionable information.
The current process is sometimes even run in a fashion that lacks any coherent categorization: Think of a drone tracking a vehicle leaving compound in Iraq, which then becomes correlated by signals intelligence to a known high-value individual (find and fix), of which targeting and engagement subsequently occurs.
Apparently conceding the need to evolve the model, Air Force doctrine even acknowledges that the current process is often executed out of order — a linear process executed in a non-linear manner. But this is not the only reason, nor is it the most important, to pursue change.
Growing Obsolescence
The proliferation of ubiquitous, powerful technologies is evolving the operating environment on both sides. As a result of an evolving threat environment over the past decade, acquisitions strategy has increased the procurement of stand-off weapons in order to maintain platform survivability and to continue to hold targets at risk around the globe. This shift has led to a remarkable revelation: Today’s U.S. Air Force is the smallest it’s ever been, yet it is slowly building an arsenal of approximately 25,000 stand-off weapons, including 5,000 cruise missiles — the most in its history. The world is changing, and this is not just limited to the Air Force. The Army’s investments into increasingly-capable long range surface-to-surface fires are notable, but the Navy has taken the lead with the emerging Naval Integrated Fire Control-Counter Air concept. This networked employment of systems capitalizes on technology to create long range over-the-horizon cooperative engagement — like an airborne E-2D Hawkeye linking multiple ship’s together in spotter/shooter roles, or an F-35 providing targeting data to an Aegis destroyer’s SM-6 missile.
This evolving salvo-competition force solves one challenge — access — but introduces a new one: time. The increased stand-off ranges required in contested environments inject a variable into the F2T2EA equation that was never accounted for. In this scenario, the engagement phase is the most challenging, dynamic, and encompassing portion of the kill-chain today due to the increased time between when a weapon is released and when it impacts its intended target. For example, a Mach 1 cruise missile takes 20 minutes to travel 200 miles — doubling Gen. Jumper’s “single-digit response time” premise of F2T2EA as he envisioned it nearly two decades ago — and that is just a weapon’s flight time!
Being ordained with a fleet of hypersonic weapons would seemingly solve this, but that is problematic for a variety of reasons (development lag, cost exchange, payload versus speed tradeoffs, etc.). Even direct energy weapons, which operate at the speed of light, still require consideration for range, depending on the employment weapon and vehicle — power dissipates over distance and reduces the effect.
The range/time paradigm is not the only problem technology has created for the dynamic targeting process. One of the five vectors of the third-offset strategy’s operational battle network is network-enabled weaponry. However, there has yet to be any dialogue to address the fact that this arsenal’s baseline employment surpasses the operational model that defines how they should be used.
The Navy’s Tomahawk Block IV, fielded in 2004, features two-way satellite communication to reprogram the missile in-flight toward new targets, disrupting the legacy process even more by enabling the targeting process after the engagement phase has begun. In July 2016, the Navy declared initial operational capability with the Joint Standoff Weapon C-1 — the world’s first air-delivered net-enabled weapon. This permits the weapon to not only engage moving targets, but to receive real-time tasking updates through the launch platform or alternative controller. The Air Force is following suit with its ambitious purchase of 12,000 net-enabled Small Diameter Bomb II stand-off glide weapons for the F-35 and future force.
Certainly the force of the future will not be using an information-decision modality designed in the 1990s, right? One could argue the military is in a similar position to as it was 18 years ago if it forces today’s solutions into yesterday’s processes.
Operationally Agile Solution
For years, the U.S. special operations community has embraced find, fix, finish, exploit, analyze, and disseminate (F3EAD) as an alternative targeting model. While not a perfect solution either, by taking attributes from both processes, a new kill-chain can evolve: find, fix, fire, finish, feedback (F5). In an era of buzzwords and catch phrases, it’s important to acknowledge similarities — but there are a few key distinctions between the current kill-chain models and this proposal.
As in the legacy F2T2EA process, find and fix must remain independent. Find encapsulates the unity of effort of Joint Intelligence Preparation of the Operating Environment, matching collection assets to commander’s intent and targeted areas of interest. This inevitably leads to detections, which may be further classified as an emerging target if it meets the intent. Fix is doctrinally described as “identifying an emerging target as worthy of engagement and determines its position and other data with sufficient fidelity to permit engagement.”
Track and target are no longer used. In today’s reality, if an emerging target is identified to a degree of fidelity to fix its location (whether static or mobile), it is inherently being tracked. F5 removes this nuance.
Target is removed because it has adopted conflicting definitions since the 1990’s, confusing its purpose. At the tactical level, target is defined as allocating sensors to a track of interest — the operational definition of track, arguably a subset of fix. If that’s not confusing enough, at the operational level target is described as “taking an identified, classified, located, and prioritized target; determines the desired effect and targeting solution against it; and obtains required approval to engage.” This operational-level process contains an approval practice with implicit combined forces air component commander authority, or delegated authority, which varies with rules of engagement. Thus, it should be recognized as an external variable to the process — not a step within it
Recalling the previously described weapons and their capabilities, the old engagement step in F2T2EA is too generalized to be useful. Unraveling this into two new processes — fire and finish — addresses an important distinction. One involves committing forces or resources (i.e., releasing a munition/payload/expendable), whereas the other involves employment with strike approval authorities (i.e., striking a target/firing directed energy/destructive electronic attack). This is similar to a ground element executing maneuvers to contact but then adhering to prescribed rules of engagement once arriving at the point of friction.
By using new, more encompassing terms, four of these processes become dependent variables that must always occur in the same order — find, fix, finish, and feedback — and solves one problem inherent to the legacy F2T2EA kill chain. While interesting, this is still not the compelling reason to change.
Model Malleability
Although it may appear linear at first glance, by far the most important part of the proposed F5 kill-chain is recognizing that fire becomes an independent variable (see Figure 1).
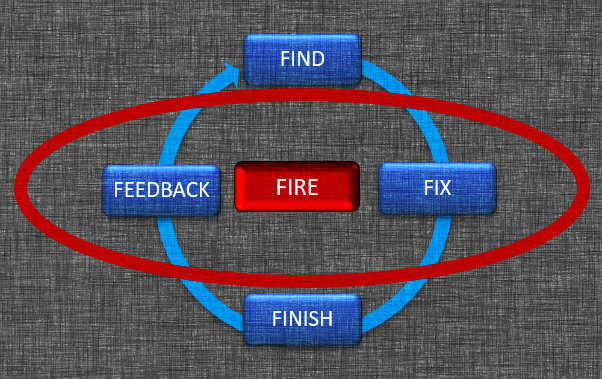
This changes the entire paradigm by injecting agility to reflect the fluid reality of warfare. A process that is malleable enough to encompass the art of the possible: This is what truly differentiates a new kill-chain and empowers an agile integrated effects loop that F2T2EA cannot provide. This is easily seen in three types of scenarios: conventional weapons employment, stand-off employment with autonomous weapons, and a semi-autonomous employment.
When fire is placed between fix and finish, it is ordered in a logical and conventional manner — supplanting the role of the legacy F2T2EA kill chain (Figure 2).
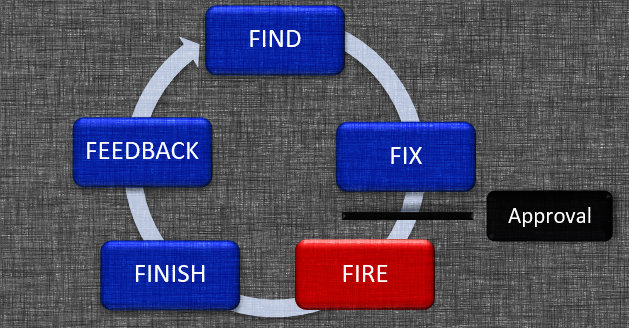
While this process is suitable for conventional munitions, older stand-off munitions such as the conventional air-launched cruise missile and even the stealthy Joint Air-to-Surface Standoff Missile are constrained to live in this model (in their current form) because of the state of the technology that existed when they were created. While forced to exist in the aforementioned time conundrum, inevitable modifications and advancements open new possibilities.
At the other extreme, we find future fully autonomous systems — both stand-off and stand-in weapons, some with “raid-breaking” capabilities. These would be committed to execute their assigned task using a different kill-chain variant (see Figure 3).
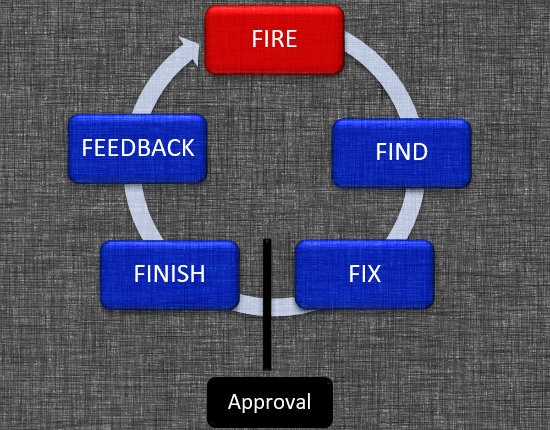
Once fired, they progress through the kill chain internally — or via a network of other autonomous weapons working together via distributed maneuver. Depending on the level of autonomous permissions granted, these weapons would send a signal back to the controlling entity once a target is fixed, along with the evidence required to garner strike approval. With approval, a command signal is sent, the weapons engage, and the kill chain is completed (finish and feedback). If they were fired with the appropriate strike approval, then they could complete the entire kill-chain autonomously without further input.
Finally, there is the middle ground. The most likely employment scenario of near-future weapons (simply because this reflects what the Department of Defense is buying today) will involve some variant of a semi-autonomous stand-off. Applied to yet another variation of the F5 kill-chain scenario (see Figure 4), once a detection is verified (find) by other surveillance resources (e.g. space), this weapon is fired and starts its journey down-range.
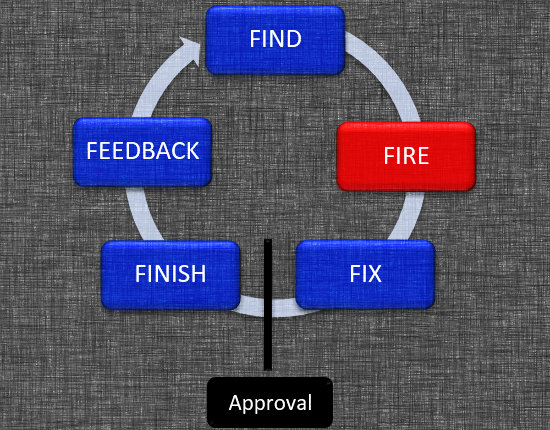
While en route, its on-board sensors work to fix the track of interest and signal it is ready to complete the remainder of the kill-chain as previously described.
It’s About Time
We have entered an era where more cognitive weapons and levels of autonomy will only be limited by policy. They should not be further hindered by self-inflicted operational constraints. The dynamic targeting model needs to evolve — it’s about time. Getting inside the adversary’s decision cycle is not unlike John Boyd’s efforts 60 years ago. The penalty of time that distance injects into the targeting process can be overcome by simply delineating employment from deployment. While three basic scenarios were covered, this model capitalizes on advances in weaponry that unlock other permutations of completing the kill-chain. Moving to an agile kill-chain provides an adaptable model that can provide a framework to solve the challenge of cross-domain synergy — the crux of multi-domain battle.
Today the joint force embraces the current F2T2EA kill-chain because the Air Force saw an operational disparity, took the lead, and developed what we have today. Eighteen years later, the Air Force must do it again. Modernizing the kill-chain today will ensure the U.S. military remains a synergized, agile, credible, and dominant force for tomorrow.
Maj. Mike “Pako” Benitez is an F-15E Strike Eagle Weapons Systems Officer with over 250 combat missions spanning multiple deployments in the Air Force and Marine Corps. He is a graduate of the U.S. Air Force Weapons School and a former Defense Advanced Research Agency (DARPA) fellow. The views expressed are those of the authors and do not reflect the official policy or position of the Department of Defense or the U.S. government.
Image: Air Force

