Intel and Attributing Bad Acts: The United States Needs to do Better

Once more, the U.S. government has missed an opportunity to make its case in the court of public opinion on an important national security matter. This time the issue at hand is the Russian hacking of Democratic Party organizations and staff–along with the leaking of information from those hacks as part of a wider effort to influence the 2016 presidential elections. As reported accurately by the mainstream American media the various documents that the U.S. intelligence community released on the subject were almost totally lacking in substance. When three Russian intelligence officers were subsequently arrested in Moscow, allegedly for providing information to the United States on Russia’s hacking efforts, this was seen by some as additional proof of the Kremlin’s involvement. But at this point, that is pure speculation and raises as many questions as it might answer. Meanwhile, the specter of Russian collusion continues to roil American politics, with Senate investigations pending and the resignation of President Trump’s national security advisor providing ample fuel to keep the issue alive.
The Obama administration’s failure to provide more compelling evidence of Russian complicity in the last days of the 44th president’s term was no surprise to those with experience in reporting on intelligence issues. Given the long-standing reluctance of the intelligence agencies to share any of their classified — and often even unclassified — products with us, are there non-governmental means of informing public debate on these crucial national security questions? Indeed, there are.
U.S. Intelligence Reports to the Public: Why Do They Come Up Short?
In the preamble to its Russian hacking report, the IC makes clear that the document will not contain any “smoking gun” evidence because of the need to protect sources and methods by which their data are collected and analyzed. Unfortunately, this reflexive protection of information routinely delegitimizes official statements pertaining to national security. In fact, the only instance of which I am aware in which U.S. intelligence seriously put their cards on the table for all to see and understand was a Security Council presentation by Adlai Stevenson, President Kennedy’s Ambassador to the United Nations. In it, he displayed to the Security Council in open session enlarged and annotated aerial reconnaissance photos clearly showing Soviet missiles and other military hardware in Cuba during the Cuban Missile Crisis in October 1962. There was an arguably more limited release of imagery by Secretary of State Madeleine Albright relating to the atrocities committed by the Bosnian Serbs at Srebrenica in 1995, but an overall lack of attribution has consistently eroded what Jon R. Lindsay refers to as the “credibility of deterrence”.
Because the current cause célèbre is cybersecurity, one might be left with the impression that this “attribution problem” is unique to that realm. This is not true. In fact, most forms of forensic intelligence analysis, including those involving the engagement of military forces (e.g. Russian involvement in eastern Ukraine) must contend with this challenge. Anonymity, which supposedly allows bad actors to attack with impunity in cyberspace is — as Kristen Eichensehr makes clear — an idea that encourages attacks. In fact, the failure to establish attribution severely limits the use of “legal tools like sanctions, indictments, or countermeasures against the attacking state.” That the same anonymity issue is involved in armed conflict situations is obvious. Being able to credibly name the perpetrator of a kinetic attack is even more important, as these usually include human casualties. Further, in complicated and politically fraught civil wars, such as those in the Balkans in the 1990s, attribution may have important geopolitical implications. They could also potentially result in war crimes charges or other punitive measures, as evidenced in the mortar attacks against civilians in Sarajevo in 1994.
The tension between protecting sources and methods and presenting a convincing attribution has arisen in non-cyber national security events as well, many of which involve Russia. One such event was the downing of Malaysia Airlines Flight 17 in July 2014 over Ukraine, which Secretary of State John Kerry immediately blamed on Russia. In so doing, Kerry made numerous references to data in the possession of U.S. intelligence that allegedly proved this unequivocally. None of the official U.S. data were ever made public. This, then, created a void that allowed the Russian government to produce not one, but two detailed publicly-released reports purporting to demonstrate that the Ukrainian government bore responsibility for the disaster.
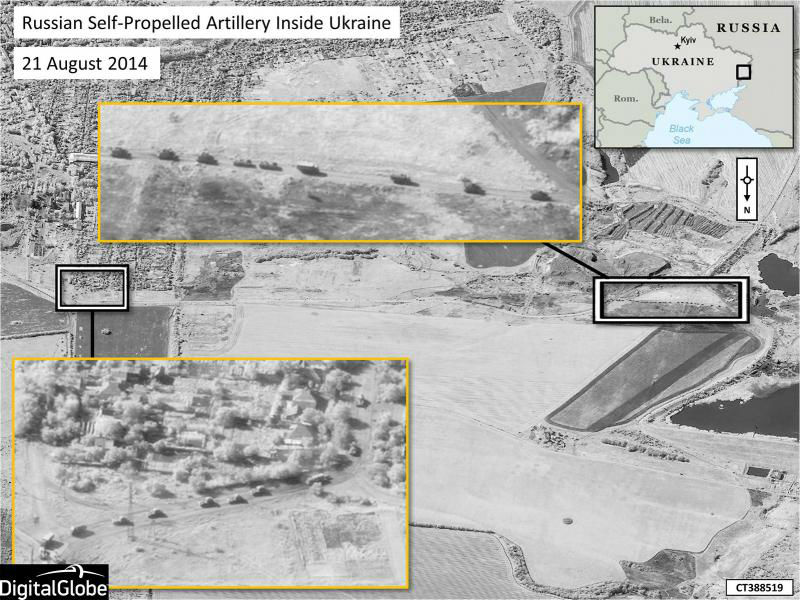
Further, when official statements regarding other Russian malfeasance in eastern Ukraine have included “proof,” their impact has been sharply limited by the public’s inability to appreciate fully what has been revealed. For example, the below NATO-released image (which is itself derived from the commercial provider DigitalGlobe and not U.S. spy satellites) purports to show “Russian Self-Propelled Artillery Inside Ukraine.” At this resolution, however, and absent more precise geo-locational information than the small reference map, for all anyone knows the picture could be of a convoy of UPS trucks in Kansas.
Time to Bring in Publicly Sourced Intelligence
The situation is not hopeless, however. Over the last three decades we have witnessed an extraordinary proliferation of public sourced intelligence, data collected, analyzed, and disseminated wholly within the public domain. Furthermore, the technical sophistication of these products has likewise increased to the point that they are far more interesting and revealing than anything released by the U.S. IC, NATO, or other official entities. To be clear, what I refer to here is not what is commonly called “open- source intelligence” or OSINT. These are products derived from public sources that are analyzed within the intelligence agencies and, despite the unclassified nature of the original information, are rarely made available to the public. By contrast, public sourced products typically come from citizen cooperatives and non-governmental organizations and exploit the wealth of data now found in commercial satellite imagery and social media. This is facilitated by burgeoning Internet connectivity both in terms of collection and dissemination, the growing ability to geo-locate events or things via GPS, the incorporation of data in geographic information systems, and the ubiquity of smart phones (especially those with video). By now, arms control/non-proliferation, humanitarian assistance, and human rights advocacy groups have advanced the use of these sources and methods to a greater degree than is true in the military affairs community. The reason for this lag is not clear, although it might stem from the affinity between the armed forces and the intelligence agencies and the willingness of military affairs analysts to accept official intelligence findings more uncritically than their counterparts in the advocacy arena.
Regardless, the citizen analysts of military affairs have made astounding progress in attributing blame to miscreant state actors in conflict zones. In particular, the Bellingcat citizen investigation journalists thoroughly documented Russian aggression in eastern Ukraine and completely debunked the Russian “evidence” on the MH 17 shoot-down. Through the analysis of “selfies” and other imagery from social media posts by Russian soldiers (to which they seem addicted) and geo-tagged photos and video, it has proven relatively easy to locate Russian personnel, vehicles, and various weapons systems within Ukrainian sovereign territory. Sean Case and Klement Anders analyzed thousands of impact craters and dozens of artillery firing positions to document cross-border attacks by Russian forces against Ukrainian units during a pivotal period in the conflict in eastern Ukraine. Nothing nearly as detailed regarding these events has been released by the U.S. or NATO. In Syria, other groups have documented the horrific acts of the Assad regime and, later, its Russian allies. Now, there are at least the beginnings of public sourced intelligence in the cyber world as well. Thomas Rid recounts how “[a]n army of investigators—including old-school hackers, former spooks, security consultants, and journalists—descended” on the hacking operation against the Democratic National Committee in June 2016 and traced it back to Russian military intelligence (GRU, or Main Intelligence Directorate) operatives.
Caveat Emptor is Still King
None of this should suggest that the current era of “digitized media ecology,” with its plethora of sources and oceans of information, is without its own nuances and downsides. As the extensive and intensive social media coverage of the Libyan and Syrian civil wars has shown, the struggle to shape international public opinion and sway interested external actors (states and NGOs) has been adroitly managed by all parties involved. Cautionary tales abound regarding the dangers inherent in accepting user-created content without thorough vetting, and there is real value in establishing a middle tier as a de facto gatekeeper. This tier would synthesize and evaluate the flood of data emanating from citizens via social media and the Internet before it is consumed by mainstream media or other users. Also, one must recognize that some gatekeepers will have a political agenda that, although not detracting from the evidence itself, may come with unsolicited commentary.
Lastly, it should be understood that information derived from public sources is forensic — it is a post facto analysis. Even still, such public sourced information is much more convincing than the thin official data that are released for the same purpose — to attributing bad acts to specific actors. Given the skepticism that abounds as to the value of officially sourced evidence and the self-imposed dictates of state secrecy, it seems clear that more public sourced evidence should be incorporated into the discourse about national security matters. That this is possible is exemplified by the work of Dutch authorities investigating the MH 17 tragedy, where competent public sources provided valuable technical expertise and evidence has been drawn principally from social media to complement official sources. The effect is powerful. The animation of the incident which features actual geo-located ground level video of the surface-to-air missile launcher vehicle entering Ukrainian territory with four missiles on board and departing later with only three can be easily understood by a lay audience.
Given that we have entered a world of “fake news,” “non-obvious warfare,” and — as Matthew Armstrong recently discussed in War on the Rocks — a “war for public opinion,” it is imperative to do a better job of attributing hostile or threatening acts if the United States and its allies wish to make a legitimate response. Encouraging the use of all available and properly validated data in a manner rigorous enough to satisfy objective analysis by non-governmental parties is a viable and much-needed approach. Doing so would further understanding of national security dynamics and perhaps convince those who might be skeptical of the propriety of one’s position.
Ralph S. Clem is Emeritus Professor of Geography at Florida International University, and is a retired Air Force Reserve intelligence officer.
Image: Kremlin.ru

